ISO 27001 Annex A control 5.23: Information security in the use of cloud services

25 August 2023.
ISO 27001: Annex A control 5.23 Information Security in the use of cloud services
Over the past year, Qudos has published a massive series of blog articles on the new version of ISO 27001. Those are all still available from links here. Now, we are going to take a deeper dive into some of the 11 new controls that were introduced in the October 2022 update. The first of those is Annex A control 5.23 Information security in the use of cloud services.
When your computer hardware and software are on-premise, it is of course, up to your business to manage and update it as necessary. As such, from an information security perspective, on-premise IT infrastructure presents a high level of responsibility.
Cloud computing and cloud services
Cloud computing allows for all or part of that infrastructure to be outsourced remotely or ín the cloud. In that event, it is managed by organizations that are expert in such things and allows your business to concentrate on what it does best. That is naturally an attractive option, and cloud computing has become almost universally adopted. While cloud computing offers many advantages, there are some information security risks that need to be considered and addressed. Control 5.23 provides a framework for doing that.
Cloud computing is often referred to by various ‘’as a service’’ names:
- IaaS (Infrastructure-as-a-service)
- PaaS (Platform-as-a-service)
- SaaS (Software-as-a-service)
They are collectively known simply as cloud services.
In IaaS, the vendor provides you with storage and other data centre facilities. You access and control various elements of the infrastructure. Well-known examples of this service are Microsoft Azure, AWS and Google Cloud.
PaaS is primarily used by software developers and programmers.
SaaS is perhaps the mostly widely used cloud service. In this case, the vendor provides you with access to a complete software application that you use via your web browser. Examples include: Google Docs, Salesforce, Gmail, Xero, Zoho, Qudos3, and numerous others.
Some products blur the line a little. Microsoft365 with its Office suite is generally considered to be SaaS. However, it also offers some platform services.
The responsibility for security in the use of cloud services is shared between the organization and the service provider - as illustrated here:
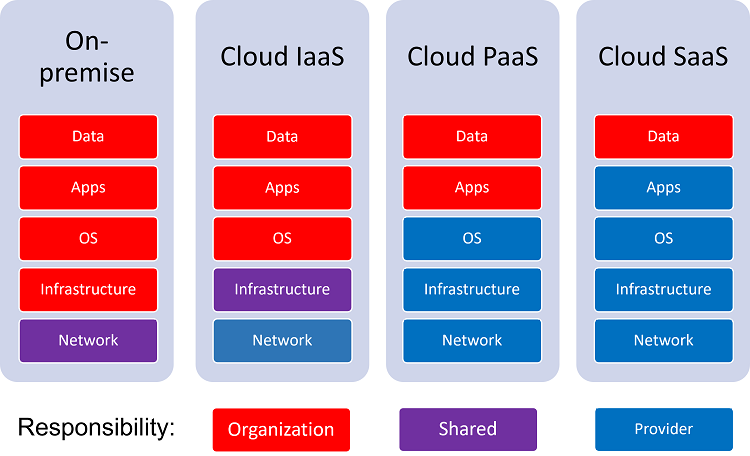
While there may be some differences in the interpretation of these services, the diagram here illustrates two clear take-aways:
- The cloud options require much less on the part of your organization
- In the cloud service models, your organization still has some responsibility – at least in controlling data input and access.
ISO 27001 Control A 5.23
This control is actually quite straightforward. It is really looking at the life-cycle of cloud services and requires that a process is established for these 4 key elements of using them:
- Acquisition
- Use
- Management
- Exit from them.
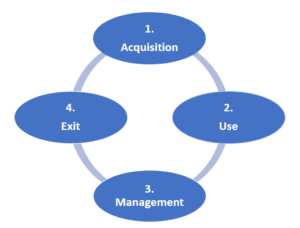
There are a couple of items we would specifically like to point out here.
- All clouds are actually on the ground somewhere, and it is becoming increasingly important to establish where the data is located. Some of your clients may require that any data you hold of theirs is located in a particular country or region.
- Its important to know what happens to your data when your organization eventually stops using the cloud service. Can you download it? What format will it be in? The time to obtain the relevant assurances is not when you do exit the service, but earlier - ideally when you make the acquisition.
While control A 5.23 refers specifically to cloud services, many other controls are also relevant when using cloud services. As security responsibility is somewhat shared with the service provider, the following controls would be especially relevant:
- A 5.19 Information security in supplier relationships.
- A 5.20 Addressing information security within supplier agreements.
- A 5.21 Managing information security in the information and communication technology (ICT) supply chain.
- A 5.22 Monitoring, review, and change management of supplier services.
Some organizations that are transitioning from the earlier version of ISO 27001 may find that their existing controls in place to address previously identified risks will also meet the requirements of that new control.

All cloud services are on the ground somewhere - the location of your data can be very important from a security perspective.
Webinar on information security in the use of cloud services.
Qudos has long been presenting webinars on information security on behalf of the Queensland Government. We presented a webinar on the topic information security in the use of cloud services on Thursday 24th August. A video recording of that webinar will shortly be made available. Contact us to request access.
Click the LinkedIn Follow button below to receive notification of further articles and webinars.
There's nothing like word of mouth to share creative content. So, if you found this blog informative, please share it with a colleague or business associate.
'ISO 27001 Information Security in plain English'
This web site includes a series of blog articles where we work through all the clauses and controls in ISO 27001. A great starting point for developing your ISMS.
It began with an introductory webinar. A copy of the slide deck is available for you here:
Ready to start your journey to ISO 27001?
The first step to commencing a management system based on ISO 27001 is to conduct a Gap Analysis. We can provide a qualified, experience certification auditor to perform a professional Gap Analysis service for you.
Contact us today to discuss your needs!

